Delivering the detail on the asset management industry
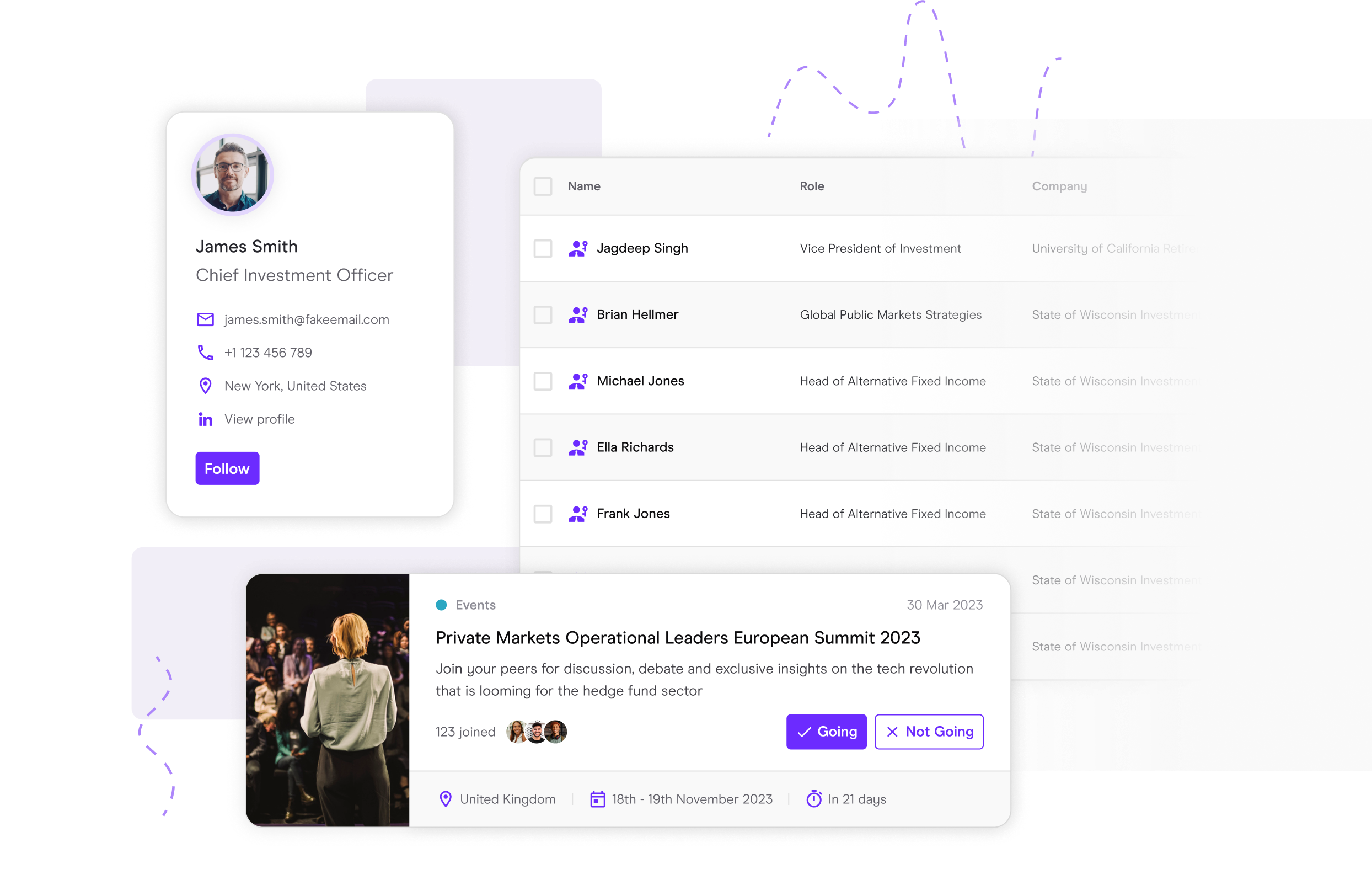
Connecting you with the right people
Our data, intelligence and networking events will help you get ahead. Connecting you with the people and data you need for more efficient fundraising, asset allocation and fund servicing.
Focusing on what you need
Our global team of industry insiders, data scientists, analysts, reporters, researchers and product developers are obsessed with your workflows. And how we can streamline them.
Plan the most effective strategy
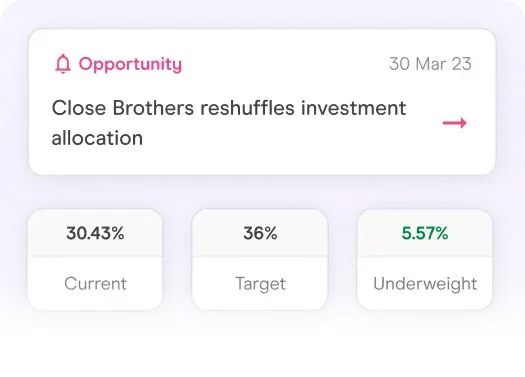
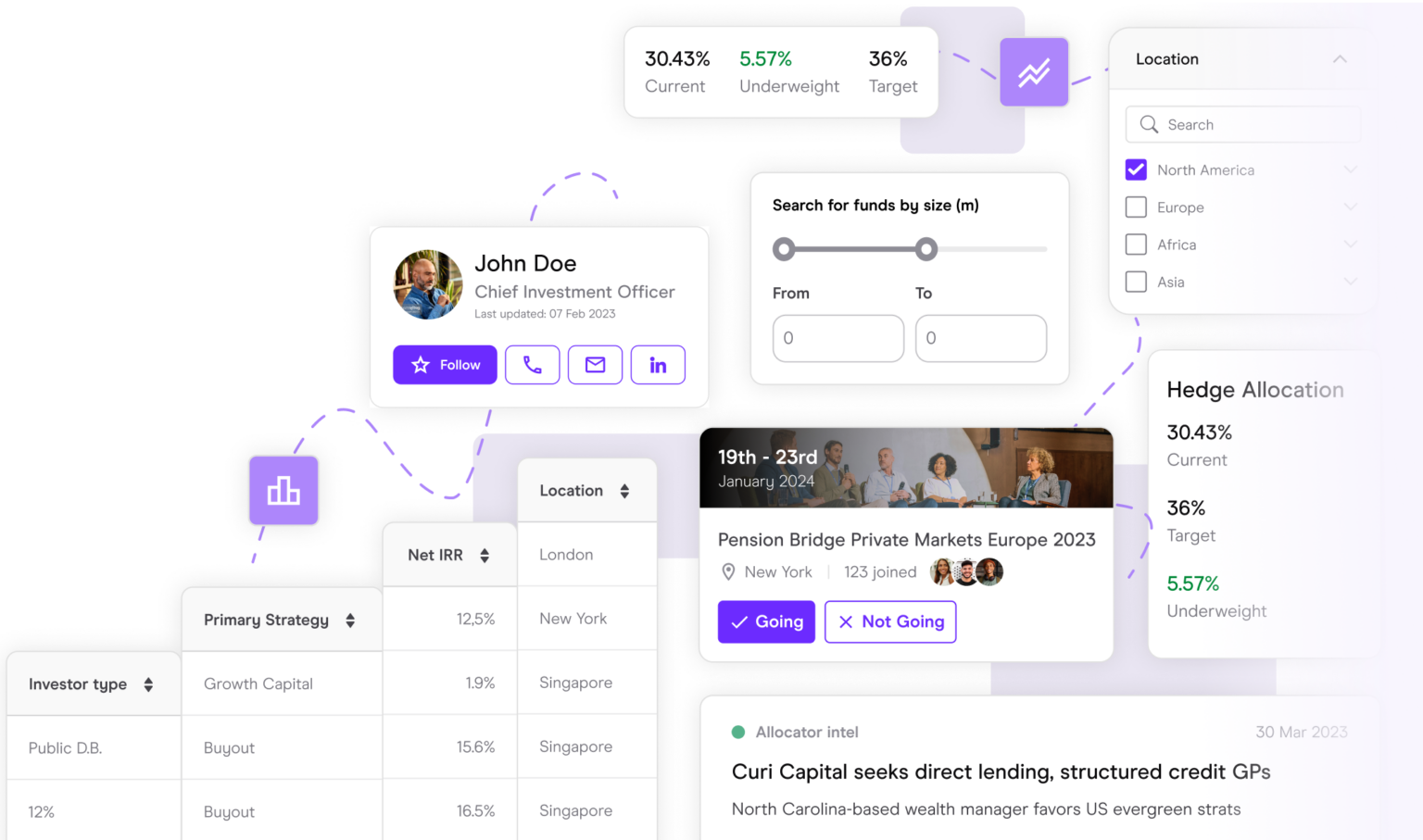
Communicate your investment strategy in the right way, attract the right investors and prioritise the right targets.
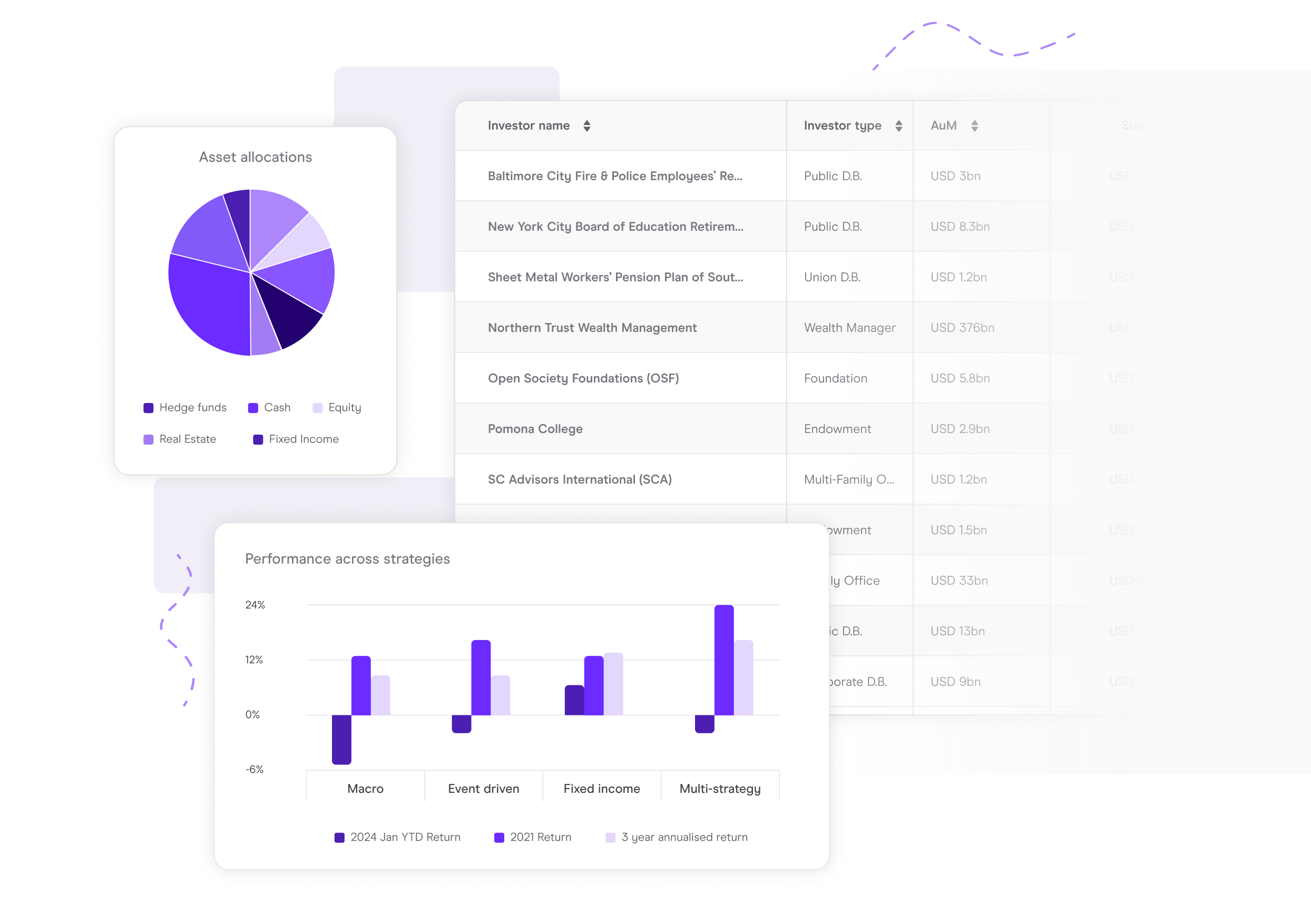
Identify the right prospects
Focus on the prospects and opportunities that are right for you. Don’t waste time chasing the wrong targets.
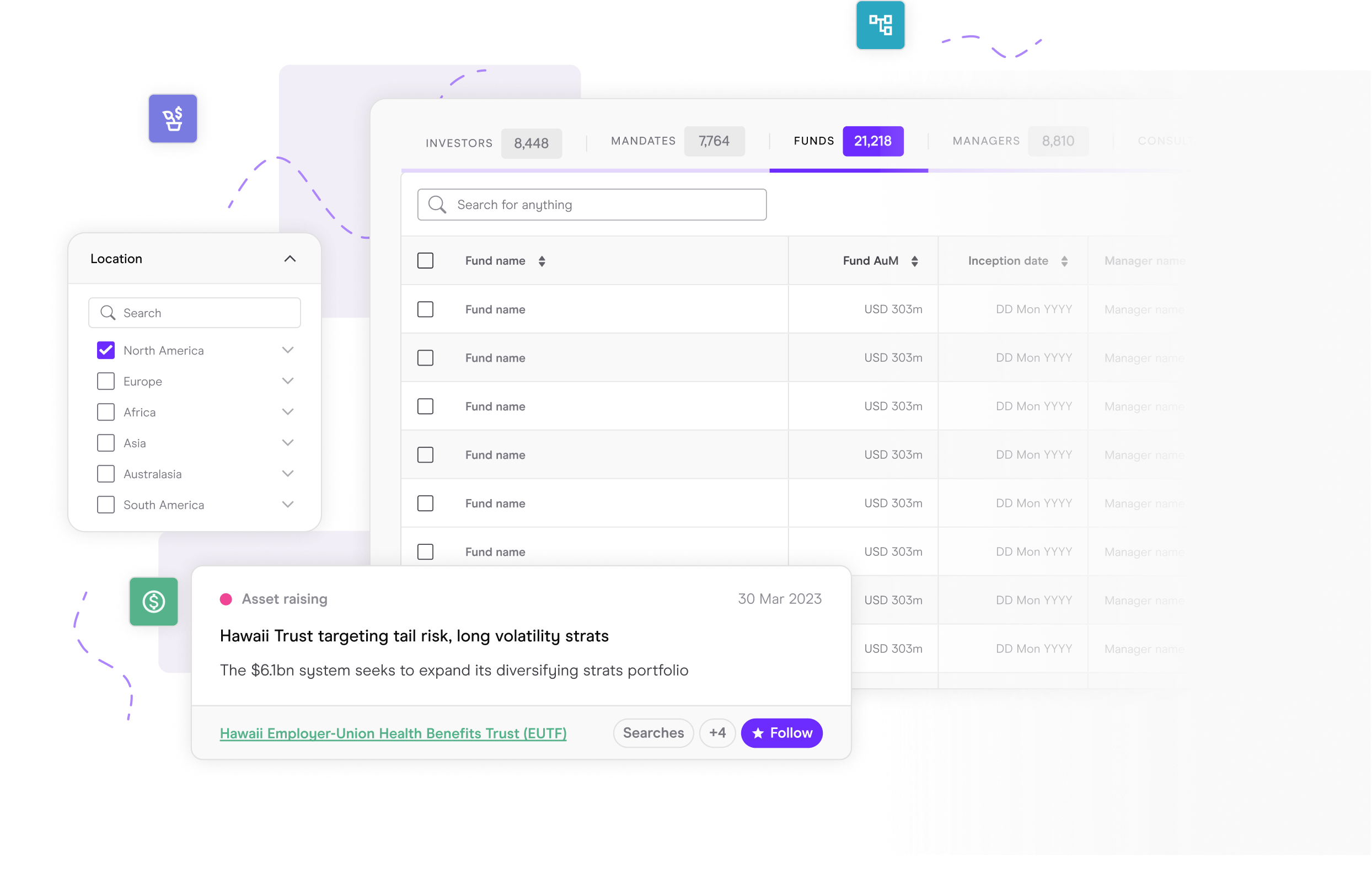
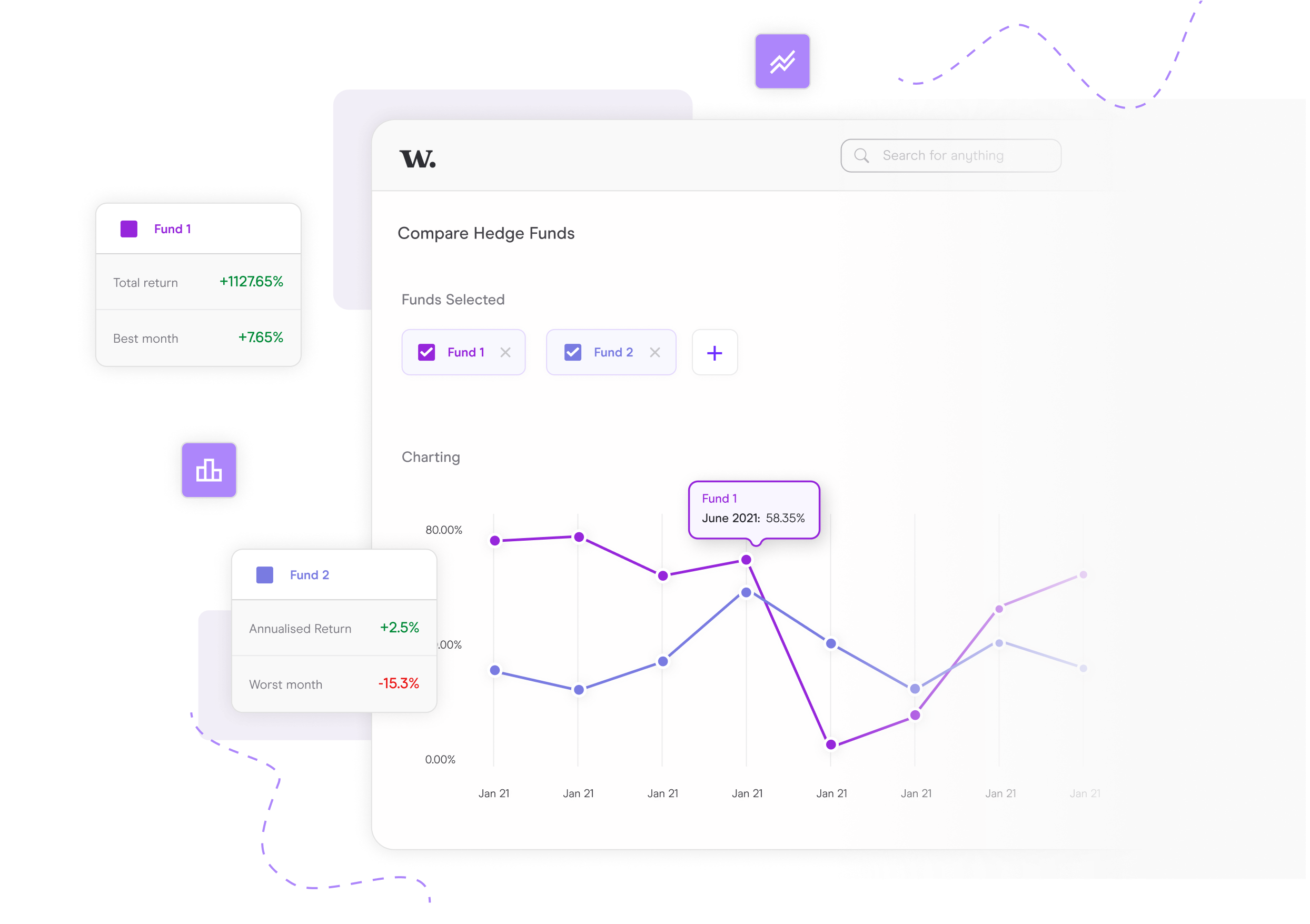
Performance and Benchmarking
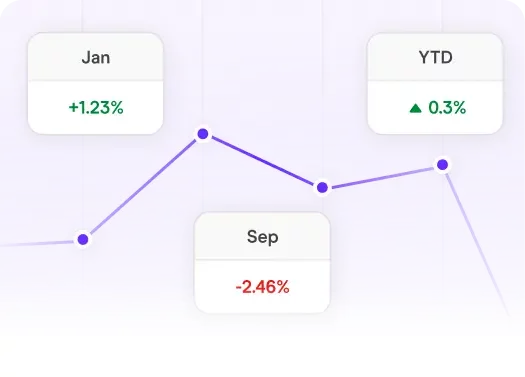
See how you shape up against the competition and know how to position your fund in the market
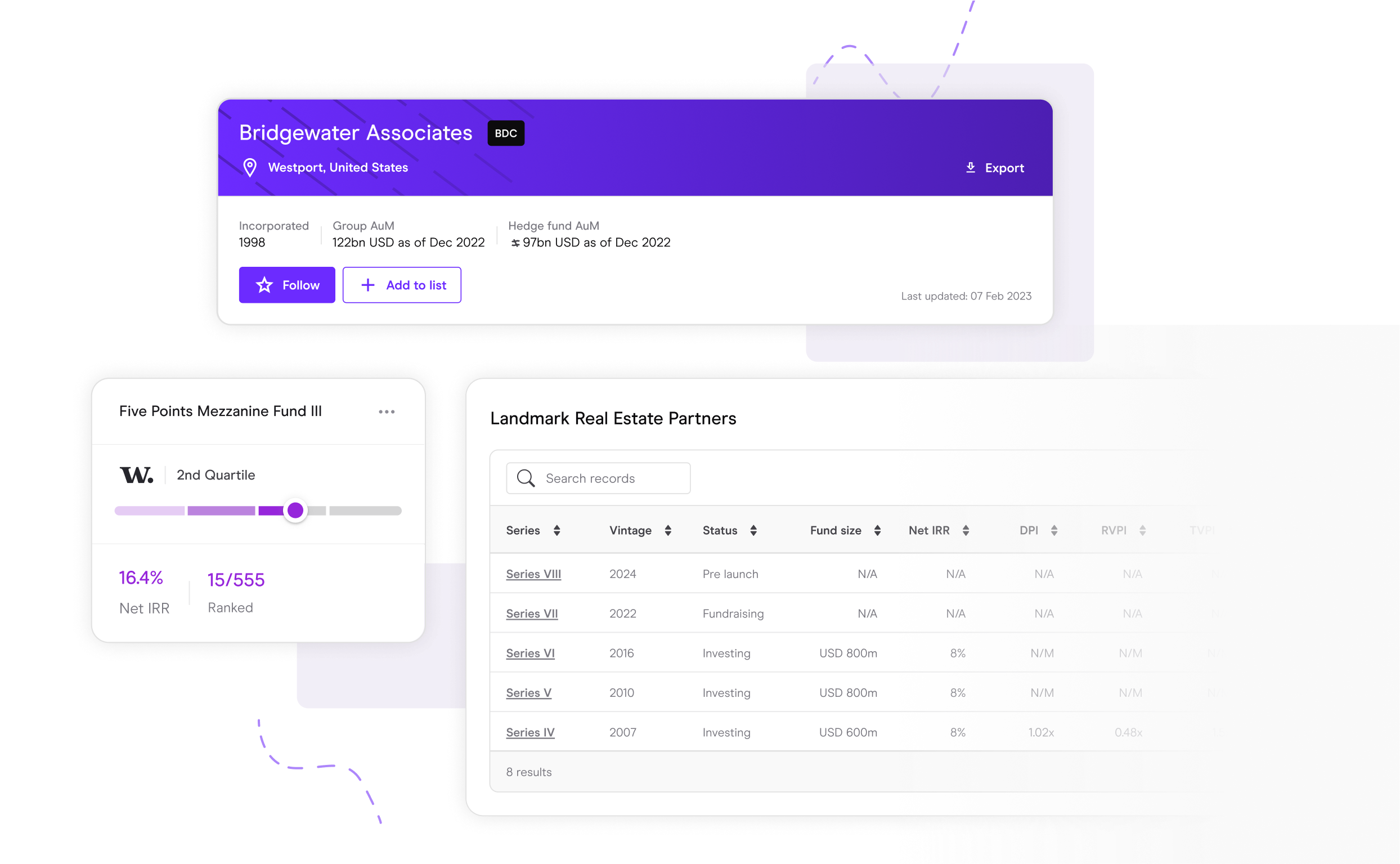
Manager selection & due diligence
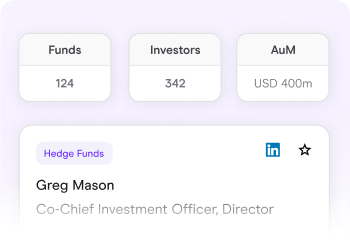
Find the managers that align with your investment strategy. Track performance, new fund launches and investment talent.
Networking
Make the right connections using our data and attending our events.
Receive weekly data highlights
Get informed. Get connected.
Create new opportunities at our industry leading events. Get connected with the people that matter. Get informed with new ideas and get inspired by leaders in your field.
Home to the industry’s leading brands




The Head of Alternatives at an institutional investment group

I absolutely love this platform. I really love it. The combination of intel, data and events is fantastic. Other products just feel dry in comparison.